Understanding Integrated Risk Management: Definition & Implementation
Integrated Risk Management (IRM) is a strategic approach aimed at integrating risk considerations related to technology throughout an organization. Essentially, IRM connects technology spending directly to the value of safeguarding resources and managing associated risks.
In this article, I delve into the essence of IRM, covering its key components, benefits, distinctions from other risk models, and various IRM frameworks. Additionally, I provide insights into the steps required to effectively implement IRM, highlight best practices, and suggest avenues for obtaining IRM certification.
Key Components of Integrated Risk Management:
- Business Objectives: These define an organization’s goals beyond mere financial metrics, focusing on delivering maximum value to shareholders. For instance, a clothing brand may prioritize developing unique designs, while a 911 call center might emphasize high service availability and rapid response times.
- Operations Systems: These are the mechanisms through which business objectives are achieved, utilizing people, processes, and technology. For example, a clothing brand employs traditional and computer-aided design processes, while a 911 call center relies on a robust phone system and trained staff.
- Critical Risks: These are significant and probable threats to operations systems or business objectives. For instance, the clothing brand may face risks such as design theft or marketing data loss, while the 911 call center is concerned about utility disruptions or system crashes.
- Mitigating Controls: These controls aim to prevent or minimize risks. The clothing brand might implement physical security measures and data backups, while the 911 call center deploys power generators and redundant systems.
- Threat Monitoring: This involves monitoring risks and controls to anticipate or detect potential issues. For example, the clothing brand may use surveillance cameras and data loss prevention technology, while the 911 call center relies on weather forecasts and network monitoring.
- Threat Response: After identifying a threat, organizations must respond promptly. For instance, the clothing brand would restore data in case of a computer crash, while the 911 call center would activate generators during a power outage.
- Feedback Reporting: This involves delivering monitoring results to relevant stakeholders for action or control adjustments. For example, the clothing brand might install window covers based on surveillance footage, while the 911 call center might enhance fuel reserves in response to generator issues.
By understanding and incorporating these key components, organizations can effectively embed risk considerations into their use of technology, ultimately enhancing overall risk management and resilience.
Discover the Top 5 Benefits of Integrated Risk Management (IRM)
Integrated risk management (IRM) offers a plethora of repeatable and measurable advantages, ranging from seizing new opportunities to establishing clear priorities, and enhancing security, performance, and resilience.
Unlock Additional Upside Potential
While many risk strategies focus solely on mitigating downside risks, IRM takes a broader approach by acknowledging and fostering upside risk opportunities. For instance, by deploying peak-time computing resources, companies like Amazon not only mitigate operational risks during peak seasons but also capitalize on the chance to lease surplus computing power and innovate through AWS cloud computing services.
Gain Clarity in Prioritization
The IRM framework assigns value to data, systems, and associated risks, facilitating transparent and justifiable prioritization. This value-centric approach enables seamless communication across the organization, ensuring alignment of objectives across operations, security, and finance functions.
Enhance Security Measures
A comprehensive IRM approach results in robust network security, incorporating layers of physical and diverse network security solutions to safeguard assets against various risks. These protective measures undergo rigorous testing and continuous monitoring, culminating in heightened and fortified security measures overall.
Optimize Operational Performance
Complexity within systems can introduce vulnerabilities and obscure critical data pathways. Integrated risk management identifies and eliminates unnecessary complexities, streamlining risk analysis and threat mitigation processes, which in turn may lead to enhanced operational performance as an ancillary benefit.
Boost Overall Resilience
By anticipating and proactively addressing potential issues that could disrupt operations and security, effective IRM bolsters organizational resilience. Systems become more robust and efficient, experiencing fewer breakdowns and quicker recovery times, ultimately enhancing overall resilience against unforeseen challenges.
Explore the myriad benefits of integrated risk management and leverage its potential to fortify security, drive performance optimization, and cultivate a culture of resilience within your organization.
Exploring ERM, IRM, GRC, and SRM: Understanding the Differences
When it comes to managing risks, various strategies aim to utilize threats to business processes effectively. The ultimate goal is to prioritize security controls, ensuring genuine security rather than mere checkbox compliance. Let’s delve into the distinctions among these common risk management practices:
Enterprise Risk Management (ERM): ERM primarily focuses on minimizing tactical and operational risks to achieve business objectives. It places less emphasis on technology, strategy, or data aspects.
Integrated Risk Management (IRM): Unlike ERM, IRM evaluates daily risk impacts, particularly through the lens of specific technologies, rather than from a broad perspective encompassing data, business objectives, or strategy.
Governance, Risk, and Compliance (GRC): GRC primarily revolves around tracking data risks within a daily regulatory context. It pays less attention to technologies, strategies, and overarching business goals.
Strategic Risk Management (SRM): SRM places strategy at the core of risk analysis. It is less concerned with risk minimization or achieving specific business objectives, and it does not prioritize particular data types or technologies.
Integrating IRM with Compliance & Regulatory Requirements
Compliance and regulatory requirements in data security focus on specific risks associated with particular assets. To seamlessly integrate these requirements into IRM, it’s crucial to assess and quantify these risks, linking them with specific systems and controls.
For instance, regulations like the Health Insurance Portability and Accountability Act (HIPAA) mandate protection of personal health information, imposing penalties for data breaches or inaccessibility. IRM addresses HIPAA data requirements by meticulously tracking associated repositories, transmissions, and systems, while also estimating risks linked with HIPAA fines. This approach leads to escalated risks, subsequently influencing security budgets. IRM tracks, monitors, and reports on each data type, system, or control to ensure compliance with regulations.
Understanding Integrated Risk Management Frameworks
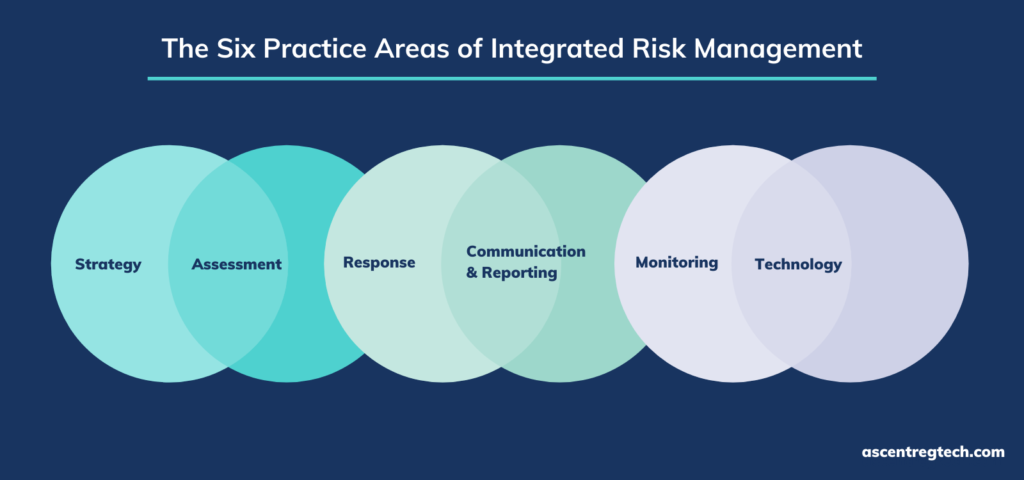
IRM frameworks offer structured processes to implement IRM systematically across an organization. Without such frameworks, organizations may grasp the concept and benefits of IRM but lack the means to execute it effectively. While certain risk management tools may provide vendor-specific risk frameworks, these tools only offer a partial solution. Comprehensive frameworks must encompass six key stages to develop an effective IRM program:
- Planning Phase: Develop a strategy and assess potential risks.
- Implementation Phase: Apply risk mitigation measures and monitor outcomes.
- Management Phase: Respond to incidents promptly and report status updates.
By comprehending the nuances between ERM, IRM, GRC, and SRM, and integrating them effectively with compliance requirements, organizations can develop robust risk management frameworks tailored to their specific needs and objectives.
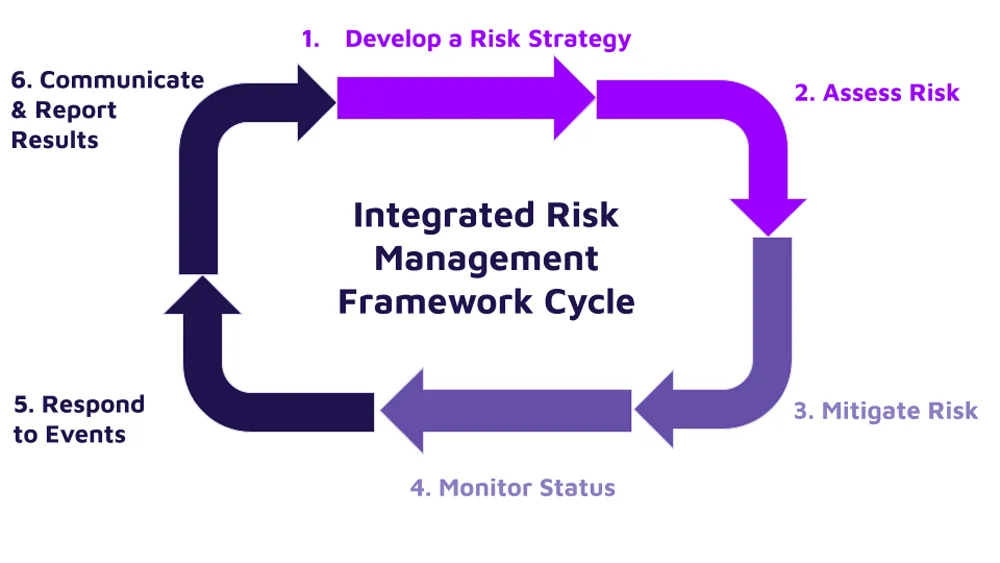
- Crafting a Risk Strategy
Commencing the Integrated Risk Management (IRM) framework involves a strategic planning phase where objectives and scope are meticulously documented. The scope can vary from encompassing the entire organization to specific divisions, systems, or datasets. It’s crucial to gather input from all stakeholders within the determined scope, including operations, leadership, process owners, IT security, and occasionally, vendors or customers. Ensuring that every stakeholder comprehends the correlation between risk and their respective objectives and responsibilities enhances their buy-in towards the IRM strategy.
During this phase, considerations regarding governance and compliance are integrated, and the risk appetite, delineating the maximum acceptable loss, is established. All objectives concerning business, operations, and cybersecurity risk management should be clearly defined and quantifiable for effective reporting. Each component within the scope should be linked to a business objective to ascertain the potential ramifications in the event of compromise.
- Evaluating Risk
The planning stage extends into a comprehensive risk assessment of the various elements identified within the strategic development phase. Risk assessments delve into individual risks as well as their combinations, encompassing both negative risks, such as business losses, and positive risks, such as business gains. The objective is to compile a risk register encompassing data, individuals, processes, and systems associated with the IRM scope.
Efforts should be directed towards making risks measurable, preferably quantifiable, by utilizing metrics such as probability and monetary values. While qualitative risk assessments may be expedient, they lack tangibility and do not facilitate a genuine understanding of risk appetite. Both internal and external risks must be evaluated, recognizing that events like data breaches and natural disasters like hurricanes can significantly impact business operations.
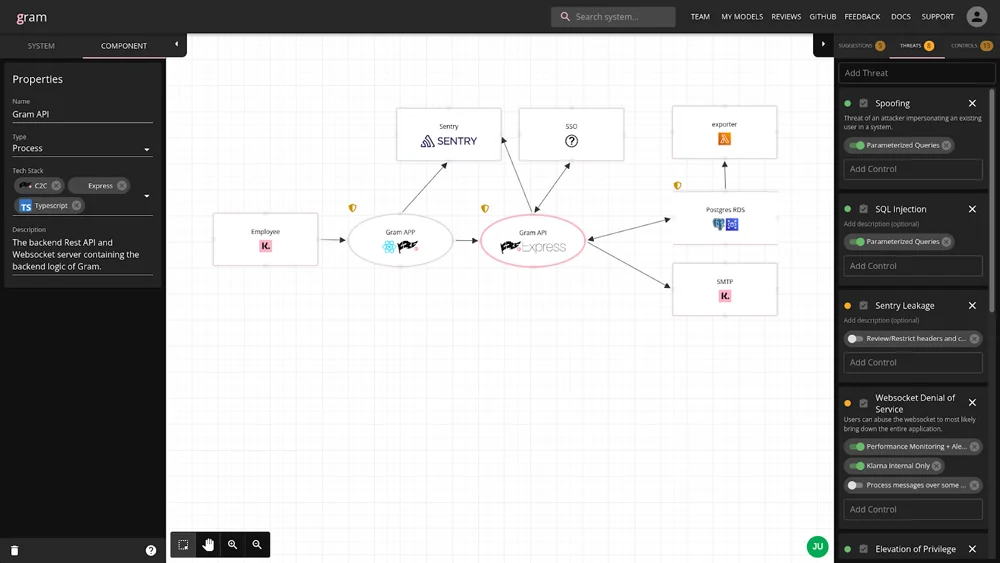
Numerous tools, both paid and free, are available to facilitate this phase of the IRM process. For instance, Klarna recently introduced Gram, a visual tool designed to correlate risks with systems and data flows, which is available for free download from GitHub. Whether leveraging an automated risk assessment tool, an IRM software solution, or a freely accessible program, it’s imperative to meticulously map out data flows and identify all potential points of failure.
- Implement Risk Mitigation Measures
Transitioning from theory to action, the risk mitigation stage within the Integrated Risk Management (IRM) framework is where strategies are put into practice. Following the risk assessment phase, which generates a comprehensive risk register, the identified risks are compared against the established risk appetite developed during strategic planning. Risks exceeding the predefined risk appetite must be either eliminated or minimized during this risk mitigation phase.
Stakeholders convene to brainstorm effective risk management strategies, which may involve implementing controls, adjusting processes, obtaining insurance coverage, or making significant business decisions such as discontinuing credit card payment acceptance. The primary objective of this stage is to develop a prioritized set of optimal risk control options.
- Continuous Monitoring of Security Controls
While established security controls are expected to mitigate risks, it’s crucial to institute continuous monitoring to validate their effectiveness. This implementation phase of the IRM framework emphasizes the importance of verifying whether controls are functioning as intended. Continuous monitoring facilitates the detection of system failures, signs of compromise, vulnerabilities, and deviations in operations.
Various forms of monitoring, including vulnerability scans, penetration tests, compliance audits, and network monitoring, contribute to network security surveillance. Each monitoring method yields metrics and reports essential for validating existing controls, identifying potential threats, and anticipating system failures.
- Swift Response to Risk Events
Upon detection of a risk event through monitoring (such as device failures, potential attacks, or exposed vulnerabilities), swift and decisive event response measures are essential to mitigate risks and minimize damages. It’s imperative to establish a robust incident response management phase within the integrated risk management framework proactively, even if it may not be frequently utilized.
Preparedness is key; hence, incident response plans should be pre-established for foreseeable events (e.g., ransomware attacks, firewall zero-day vulnerabilities). This preemptive approach eliminates time-consuming decision-making processes during critical moments, such as determining which executives to notify, when to engage cybersecurity insurance providers, or when to enlist external incident response teams. Although no plan can cover every eventuality, leveraging existing plans enables faster responses, thereby mitigating potential damages.
- Effective Communication and Reporting
The final stage emphasizes the importance of effective communication and reporting, which builds upon the insights gleaned from continuous monitoring and event response efforts. Regular monitoring generates status reports and penetration test reports that validate the efficacy of existing controls, while each event response generates incident response reports detailing the entire incident management process.
Clearly defined metrics are essential for generating regular reports used in decision-making processes, compliance reporting, and board of directors’ briefings. Stakeholders require concise communication summaries that encapsulate these reports at a suitable technical level and depth of detail. A comprehensive IRM system facilitates organization-wide reporting to enhance employee training initiatives and foster a culture of risk-awareness.
Unlocking Success: Top 5 Best Practices for IRM Implementation
Merely adhering to a framework won’t suffice to elevate risk management practices. Effective IRM implementation hinges on embracing best practices that serve as the foundation for success. These practices are tailored to seamlessly integrate IRM with business operations, streamline asset classification, centralize management processes, standardize operational procedures, establish detailed connections between systems, leverage information effectively, involve all relevant stakeholders, and prioritize IRM within the organization’s focus.
- Categorize Resources:
Organize assets and data types into distinct categories customized to the organization’s needs. This categorization establishes a taxonomy that fosters a shared understanding of systems across different departments, facilitating the identification and elimination of redundancies. Consistent terminology minimizes confusion and enhances internal communication, promoting alignment with the board of directors’ objectives. - Centralize Management:
Consolidate authority, data flows, repositories, and systems management to eliminate redundancies and ensure consistent governance across silos. Centralization reduces the attack surface for critical resources and can yield cost savings by eliminating redundant storage, tests, or reports. - Embrace Standardization:
Adopt standardized event response processes, monitoring criteria, testing protocols, and reporting frameworks to enable automation and expedite decision-making. Standardization fosters objectivity, quantifiability, and comparability of data across the organization, enhancing analysis and facilitating uniform decision-making. Streamlining routine tasks frees up time for strategic endeavors and addressing exceptional circumstances. - Formalize Connections:
Identify and document dependencies, connections, and data flows between resources to identify redundancies, security gaps, and relevant stakeholders. By formally establishing relationships, organizations can better align risks with goals, key risk indicators, and business activities, fostering a deeper understanding of business operations for all stakeholders. - Involve Stakeholders:
Foster a risk-aware culture and enterprise-wide accountability by engaging internal and external stakeholders in IRM development and ongoing revisions. Leveraging cross-functional teams harnesses diverse knowledge to create accurate system maps and comprehensive risk assessments. Wide participation ensures the accuracy and effectiveness of risk management efforts and reduces resistance to implementation.
By adhering to these best practices, organizations can optimize their IRM implementation, enhance risk management processes, and cultivate a culture of proactive risk awareness across all levels of the organization.
In Conclusion: Integrated Risk Management Safeguards Business Operations
In the realm of business, risk is an inherent component of operations. However, Integrated Risk Management (IRM) sheds light on concealed technical, operational, or enterprise risks that, if overlooked, have the potential to jeopardize success or even lead to the downfall of an organization. By embracing and implementing effective risk management strategies, companies formally acknowledge risks and establish controls to mitigate potential downsides, thereby fostering responsible growth. Incorporating IRM into organizational practices fosters a culture of risk awareness throughout the company, promoting enhanced security and alignment.